Infinity
The Unified Network Source of Truth for all your network information.
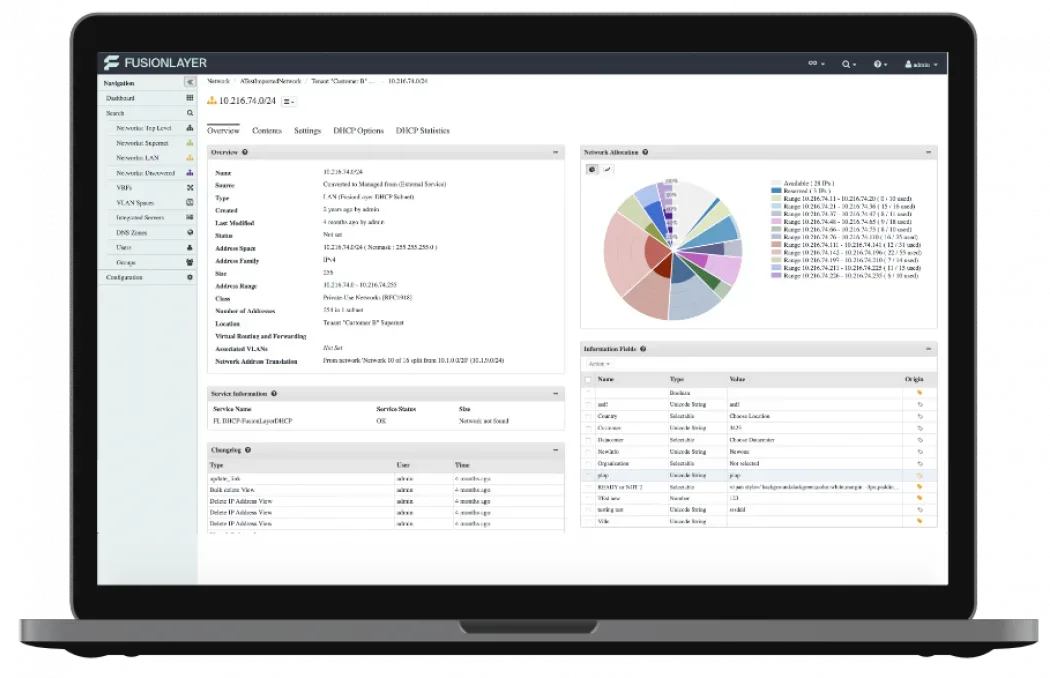
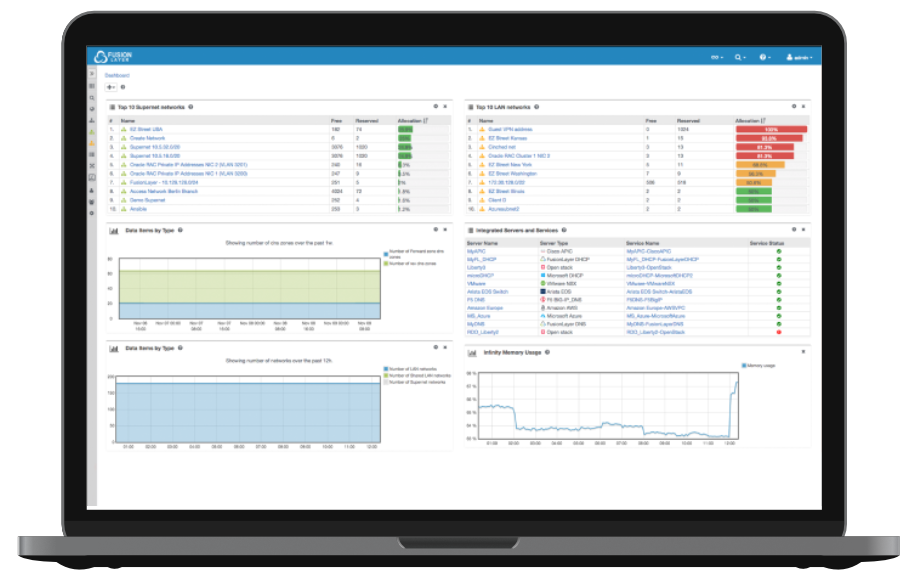
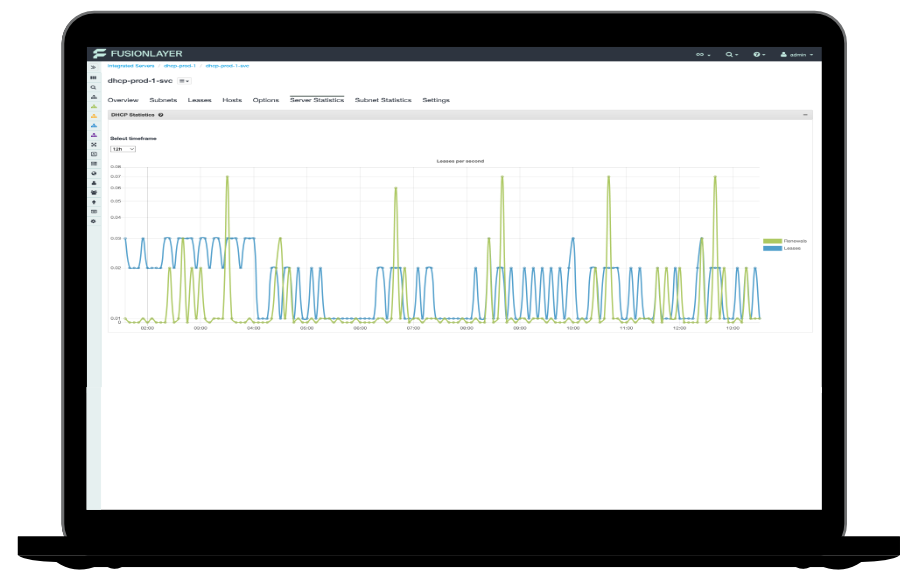
FusionLayer Infinity is the world's first Software-Defined IP Address Management (SD-IPAM) designed to replace the traditional IPAM tools and spreadsheets
Unified management and provisioning. Patented.
FusionLayer Infinity has been designed for the next-generation business infrastructures. The patented solution provides a single source of truth for all network information,including subnets, VLANs, VRFs, policies, and more. Thanks to FusionLayer Infinity s scalable solution architecture, an individual instance manages up to:
- 100,000 subnets
- 6,000 overlapping private network spaces
- Millions of overlapping IP addresses
- Dozens of overlapping VLAN spaces
- 10+ orchestrators responsible for different service platforms
Once you are managing all network data in a unified system, you gain secure access to the data through a developer-friendly REST API.